Summary
If you want to check how well SSL has been implemented for a website, you can use the excellent, free SSL Labs tool from Qualys. As their website says:
This free online service performs a deep analysis of the configuration of any SSL web server on the public Internet.
You just submit a domain name and wait a couple of minutes for the tests to complete. Scores range from A+ to F and are explained in the rating guide. It sounds good and it is.
This website (GHOST_URL/) is hosted in Azure Web Apps (Microsoft's Platform as a Service web hosting environment) and, until recently, this meant that the maximum possible score from the SSL Labs test was a B. Now that Microsoft have removed support for the insecure RC4 cipher, this website scores an A. I didn't have to do anything to bring about this improvement in security[1], it happened automatically.
Background
I took the decision to run TomSSL in Azure Web Apps partly to delegate the burden of infrastructure maintenance. As you may recall if you read my introductory blog post from last December, having full SSL support was my only real requirement for the site. However, I felt everso slightly chagrined by the fact that hosting the site in Azure Web Apps (or Azure Websites as it was called then) meant that my website only scored a B in the SSL Labs test. And it was only the support for the insecure legacy RC4 cipher which was marking me down. Getting rid of RC4 myself would have meant using a different hosting environment which would necessarily have involved some kind of maintenance being done by me, which I was keen to avoid. If only Microsoft would disable RC4 support...
Microsoft disables RC4 support
In February a request was made to disable insecure ciphers in Azure Web Apps.
Since I voted in favour of this change, I received email updates about the status of the request. One such update resulted in me writing the following tweet just over three months ago:
Looks like @Azure websites will finally be getting rid of RC4 cipher in the next few weeks. That's great! :-) http://t.co/znRPJwyUUj
— Tom Chantler (@TomChantler) June 1, 2015The rollout was to be done in stages (meaning some sites would be upgraded sooner than others) and when I checked last week, it had happened.
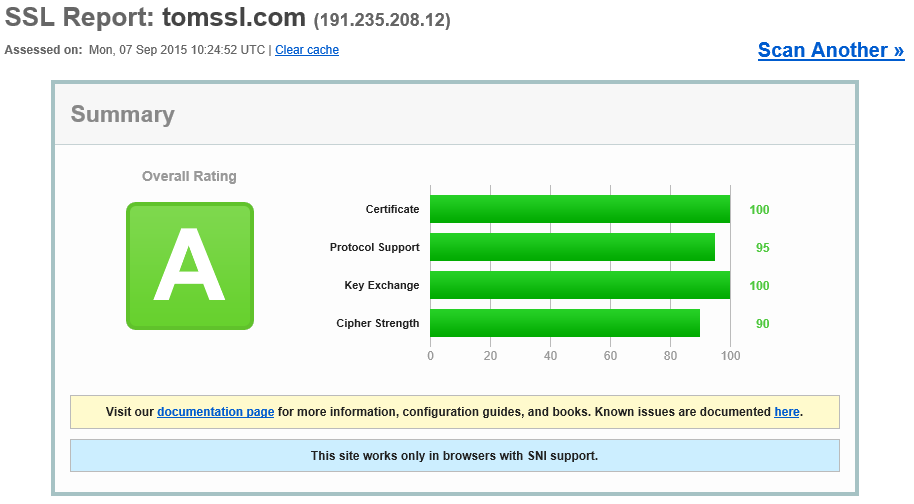
Okay, maybe it's not quite as exciting as I'm implying, but the point is that I've been busy doing other things and not thinking about the infrastructure for TomSSL. Since I knew it was going to be fine, I didn't make a note to check too often. I didn't (and don't) know or care precisely when it happened. It just magically upgraded without me even being aware of it (okay, that would be bad, but they did warn me in advance). I also didn't pay anything for this to happen either.
I realise that there are other hosting providers who take care of your infrastructure for you, but actually I can't think of any off the top of my head who provide such flexible IIS hosting. And this upgrade even applies to the free tier.
Conclusion
Azure Web Apps is a convenient, low-maintenance way of hosting your web applications.
The idea of what constitutes a good SSL implementation is constantly in flux as new security exploits are discovered with disconcerting frequency. Azure Web Apps is responsive to these changes and has recently disabled the RC4 cipher to ensure that their implementation is compliant with current best practices.
The cool thing is that everything was upgraded automatically and I didn't need to do anything. This is what cloud computing should be about in my opinion[2].
You can check how your SSL implementation measures up against current thinking by using the free online SSL Labs tool. At the time of writing, this site gets an A.




