Yesterday I heard about a vulnerability in the WPA2 WiFi protocol which seemed to signify that even the secure version of WiFi... isn't. The most salient point seems to be that "attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted." This sounds pretty bad.
You can read more about it here: https://www.krackattacks.com/ and I recommend that you do as it's nicely written and fairly easy to digest. Kudos to Mathy Vanhoef for his work both in discovering and documenting the attack.
So what can we do?
Let me repeat the first Q&A point from the website:
Do we now need WPA3?
No, luckily implementations can be patched in a backwards-compatible manner. This means a patched client can still communicate with an unpatched access point (AP), and vice versa. In other words, a patched client or access point sends exactly the same handshake messages as before, and at exactly the same moment in time. However, the security updates will assure a key is only installed once, preventing our attack. So again, update all your devices once security updates are available. Finally, although an unpatched client can still connect to a patched AP, and vice versa, both the client and AP must be patched to defend against all attacks!
Ordinarily, at this point I'd start crying into my beer as I'd have a fairly strong suspicion that my network equipment was unlikely ever to be patched. However, if you have Ubiquiti kit, then you're in luck as they have already released a patch.
Ubiquiti UniFi
I've recently started buying UniFi kit from Ubiquiti. This stuff is all the rage these days and for good reason; it's very good and is very well supported. I reckon I'd describe the UniFi range as prosumer kit.
So far, I've only bought a few items, so I won't bore you with all the details (although it's quite likely that I will on another occasion). I've got these:
- UniFi Security Gateway (USG)
- UniFi Cloud Key (UC-CK)
- UniFi AP-HD (UAP-AC-HD) - this is my wireless access point
- An old generic gigabit switch
- An old BT OpenReach VDSL/FTTC modem
In a nutshell, everything is connected to the switch except the modem which is connected directly to the WAN port of the Security Gateway. The Cloud Key "securely runs a local instance of the UniFi Controller software and features cloud Single Sign-On for remote access" which means I can login to it from anywhere and administer my home network, which is nice.
This meant that as soon as I discovered that a patch had been authored, I was able to log on to my home network from wherever I happened to be (which was not at home) and see if the update was waiting for me. It wasn't.
Ubiquiti are rolling out firmware updates as I type. If yours isn't there yet, check out their blog post linked in the tweet:
Firmware Update 3.9.3.7537 includes security patch for the WPA2 vulnerability called #KRACK More info > https://t.co/lc9ODD5U1e
— Ubiquiti Networks (@ubnt) October 16, 2017
So how can I force the update?
This is what I did.
First I went to https://unifi.ubnt.com and logged in.
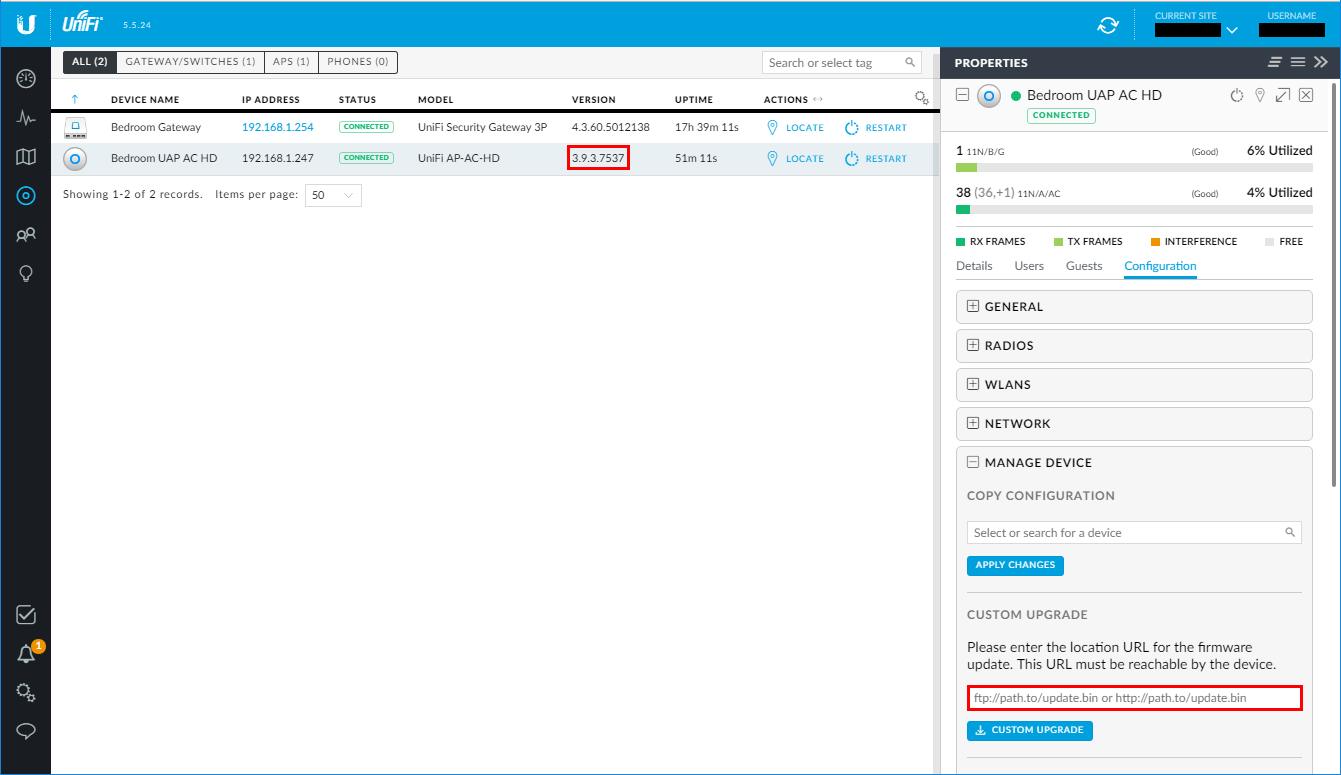
Then I launched my dashboard (effectively logging in to my Cloud Key) and noticed that my access point didn't have the latest firmware and didn't yet say there was an update pending.
I clicked on Devices and then on my access point and went to Configuration → Manage Device and pasted the URL to the custom firmware from the Ubiquiti blog which, in my case, was this one: UAP-AC-HD/SHD. Then I clicked Custom Upgrade.
And that was pretty much it, a few minutes later, my device dashboard looked like this:
Conclusion
It's worth buying decent network hardware.

